Erdstall is a Blockchain scaling solution using Trusted Execution Environments and is based on research results of the Chair of Applied Cryptography at the Technical University of Darmstadt, Germany.
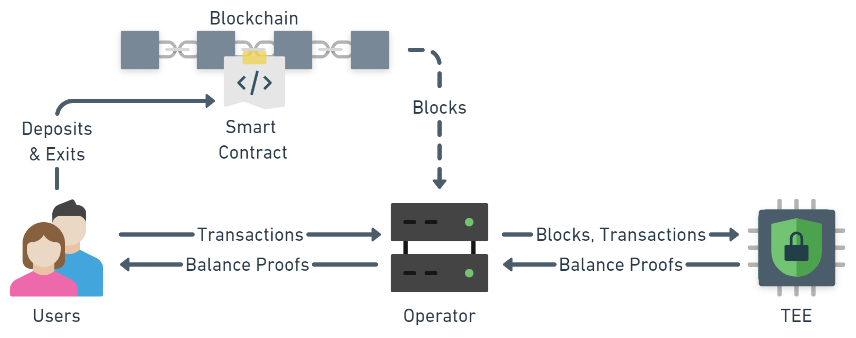
Users can join and leave the system by depositing assets into or withdrawing assets from the Erdstall smart contract. They can send transactions to each other by sending them to the untrusted Erdstall Operator.


Users deposit their funds into the smart contract to join the Erdstall system. After the deposit, the contract holds the funds while they are processed off-chain. The Erdstall smart contract defines how the funds are unlocked and the challenge-response logic in case of wrong behaviour by the operator. Users also exit the system via a withdrawal from the smart contract.
The Operator forwards all new Ethereum blocks and all off-chain transactionsfrom users to the secure enclave. After each transaction phase he receives balance proofs from the secure enclave and sends them back to the Users. It is important to know that the operator doesn’t need to betrusted! He can decide not to forward any information, but cannot forge messages or alter the state of the Erdstall system.


The TEE runs the Erdstall Kernel inside a secure enclave, which processes all transactions in the system. After each transaction phase it generates and sends balance proofs as well as exit proofs to users that want to leave the system.
Computation results can't be changed by any outside influence.
All computation and state is kept hidden from the operator
Users can verify that the operator is running the correct Erdstall kernel inside his TEE
Erdstall proceeds off-chain in so-called epochs, which span a fixed length of Ethereum blocks. At the end of each epoch, the TEE generates balance proofs for each user, which the operator has to distribute. They can be thought of as security checkpoints with which users can leave the system in the event of a faulty operator.