cNFTs enable advanced privacy features for NFTs to push the boundaries and enable new use cases for NFTs.
Confidential NFTs allow using NFTs to control, log and manage access to valuable data, software features, restricted areas, physical devices and much more.

NFT-attached data is currently public and not bound to an NFT. By encrypting NFT data like high-resolution images, video streams or license files, only the current owner of the NFT can access them. When an NFT is traded, ownership and access privileges are transferred to the new owner.

cNFTs leverage trusted execution environments (TEEs) to make sure that only the current owner has access to the cNFT-attached data. Users can further verify that the correct software is running inside the TEE by leveraging remote attestation.
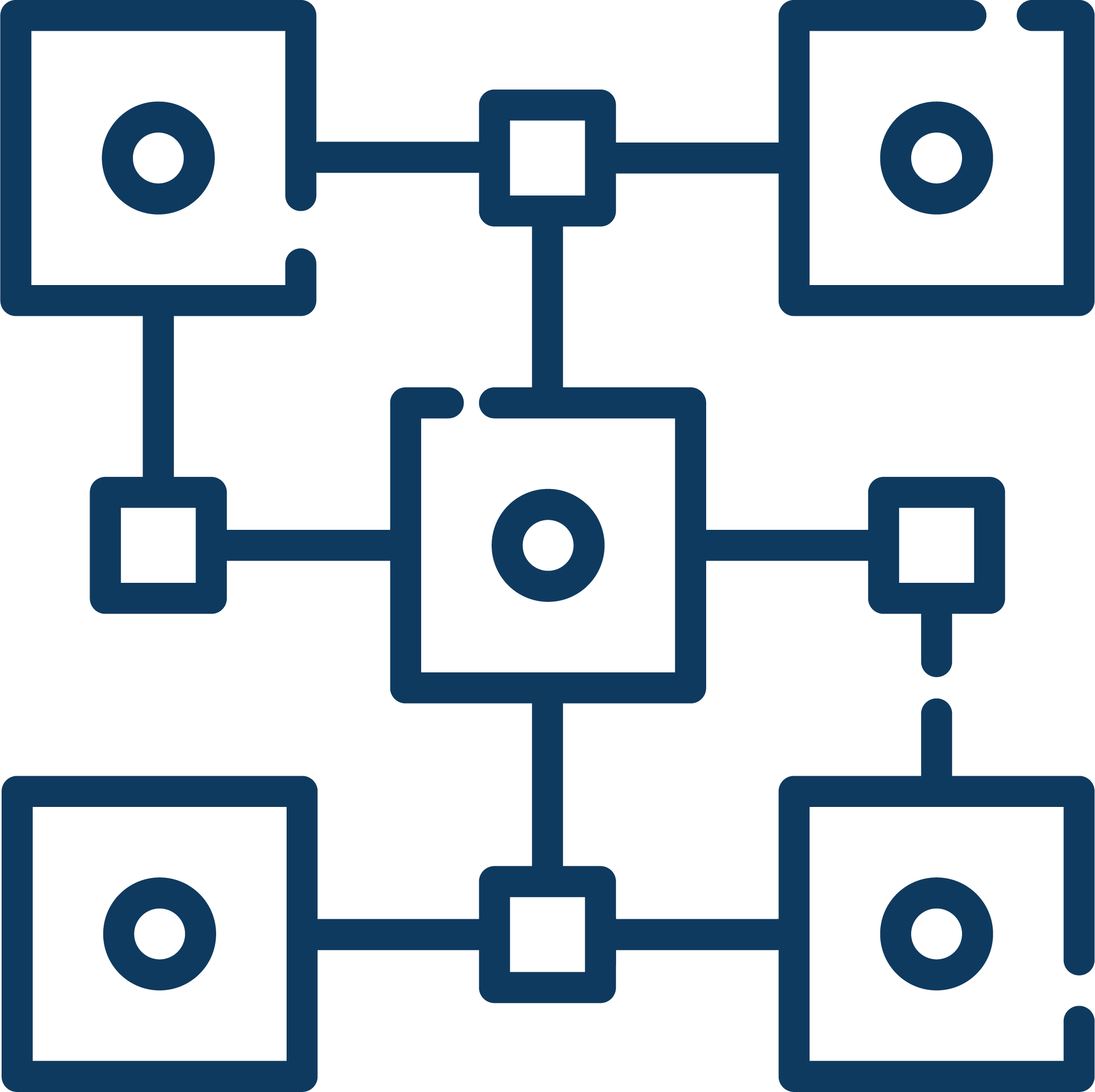
The trustless cNFT Oracle tracks the current owner of cNFTs and, for example, decrypts NFT-attached confidential data on-demand. Since the oracle runs inside a trusted execution environment, no trust in the oracle is needed.

cNFTs can be enabled as a service for marketplaces built with Nifty Erdstall. We plan to extend the service to other L2 networks in the future.
Confidential NFTs – Encrypting Confidential Data in NFTs
In the cNFT project, methods for secure and efficient creation and encryption of NFTs with encrypted metadata are being developed.
Project Description
Non-fungible Tokens (NFTs) are a new asset class that allows the creation of tradable assets from digital data, such as images or videos. Currently, the metadata associated with an NFT is publicly available, which limits its use in traditional industrial sectors. The developed solution, cNFT (confidential NFT), enhances conventional NFTs by adding an additional private storage area for storing sensitive data.
Application Area
Our cNFT solution enables numerous new use cases for NFTs. For instance, it can be used to handle access to premium content, such as exclusive clips from sports events or movies. Additionally, a cNFT can represent a software license, facilitating license management within companies and across company borders. In addition to tapping into new market segments, cNFTs significantly enhance the appeal of traditional NFT applications. For example, in widely used image NFTs, a high-resolution version of the image data can be stored in the NFT’s private storage.
Project Participants
The cNFT project is carried out by PolyCrypt GmbH, a spin-off from the Applied Cryptography department of TU Darmstadt, specializing in innovative products in IT security and blockchain technologies. PolyCrypt has successfully placed its first products in the market and currently employs 12 people. In the cNFT project, two new software components are developed to protect sensitive data within an NFT. Firstly, the “Encryption Component” encrypts the metadata and stores it in an external storage medium (e.g., a cloud solution). Secondly, the “Authentication Component” provides an interface to finely control access to the encrypted metadata. Our technology utilizes hardware security modules called Trusted Execution Environments (TEE), where software can be executed without the TEE operator having access to the execution. The cNFT technology uses TEE for metadata encryption/decryption, ensuring that only the current owner of the cNFT has access to the associated metadata.